
Brian Yu
2nd Prize Winner: $150
ABF Achievement Award, 2021 ($500 + Laptop), Northwood High School, Irvine Unified School District, Orange County
Currently enrolled with the University of California Irvine: Bachelor of Science
How Do The Hackers Target The End-Users?
Most people probably imagine a hacker as a shadowy figure that utilizes their computer abilities to access the information of large corporations or governments and steal money by breaking into digital accounts. After all incidents like Solarwinds and Colonial Pipelines make big and exciting news. However there is a growing number of hackers that don’t hack computers but hack humans.
Social engineering is the use of psychological manipulation to get a victim to give up information or do an action. Most of the time hackers use social engineering to get people to divulge their bank accounts or their social security but it can also be used to persuade people to download malicious software or give hackers a foothold with a system. While social engineering spans a number of attack vectors, phishing (and its spinoffs) are some of the most prevalent. Phishing is when an attacker sends a fraudulent message in order to solicit information from a victim and it has a big economic impact on companies. In fact Cybersecurity Dive reports that in 2021 the average cost of phishing attacks was $14.8 million for US companies. Phishing isn't just limited to enterprise targets however, many hackers target non-enterprise targets with email scams, fake text messages, and fraudulent links.
As a result it is important for people, both professionals and non professionals alike, to be capable of identifying instances of social engineering. Most of the time there are aspects of phishing attacks that make it easy to identify.
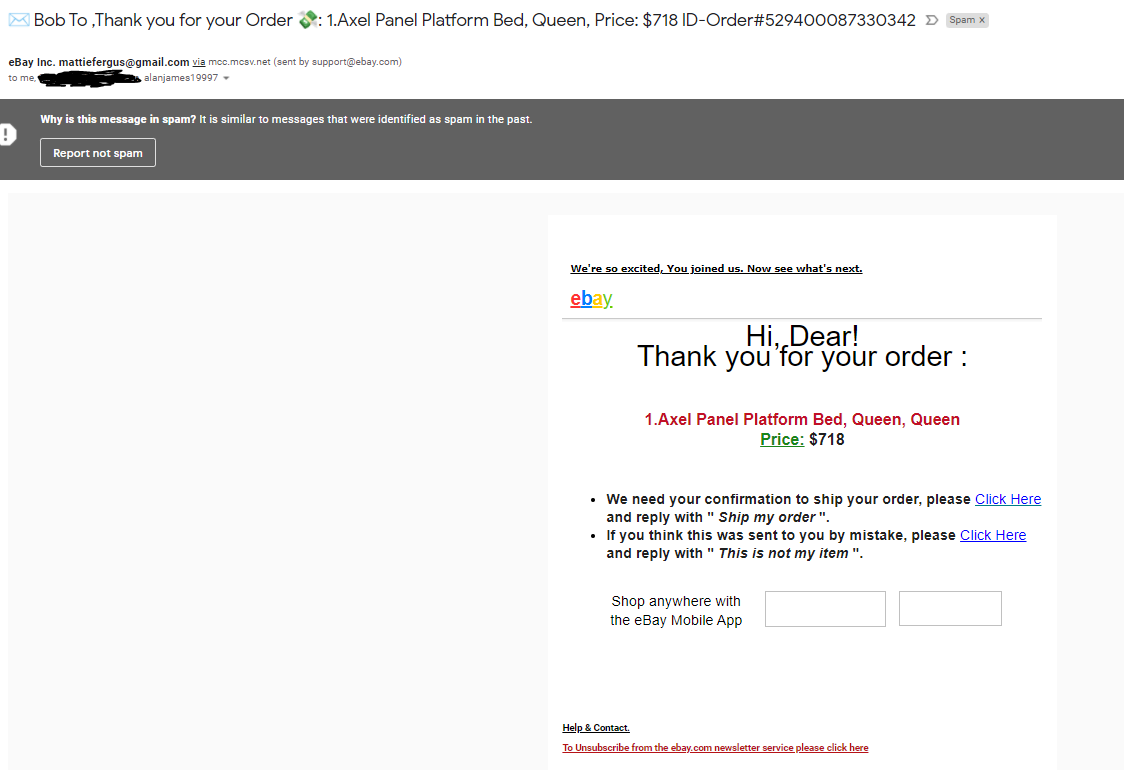
For example in the image above we see a fraudulent email that is pretending to be an ebay order confirmation. To the untrained eye it may look like an accident on the part of ebay that can be fixed by clicking the link. However there are certain aspects one can look at to determine the authenticity of the email. For example in the sent from field we see the line “eBay Inc. mattiefergus@gmail.com via mcc.mcsv.net (sent by support@ebay.com)“. This is an immediate red flag as a normal message from ebay would not include “eBay Inc. mattiefergus@gmail.com via mcc.mcsv.net” in the sender fields. As a result one can conclude that this is most likely sent from an email account masking itself as an official ebay support email. Furthermore the content of the email is poorly formatted, with the spacing between the “Hi Dear!” and “Thank you for your order” clearly off. Lastly when hovering over the link “We’re so excited”, one can see that the link does not lead to an ebay domain but rather mails the scam to other people, probably hoping to use your email to make it harder to trace it back to its origins. Even if after examining the email and determining that it is legitimate it is still safe practice to never click on links. Instead access the site in question by manually typing it in the search bar.
In a world where anyone can send an email or text masqueraded as official communications, it is incredibly important that companies prepare themselves and their employees to defend themselves against social engineering attacks. While software like email filters can be beneficial in preventing these attacks, it is important to still train employees in identifying and responding to instances of social engineering. After all security systems are only as strong as the user and it only takes one slip through the defenses to seriously harm a company.
Work Cited
Jones, David. “How Much Does Phishing Really Cost the Enterprise?” Cybersecurity Dive, 17 Aug. 2021, www.cybersecuritydive.com/news/phishing-cost-enterprise/605110/.
“Phishing Attack.” Malwarebytes Lab, Malwarebytes, blog.malwarebytes.com/101/2018/09/6-sure-signs-someone-is-phishing-you-besides-email/.
